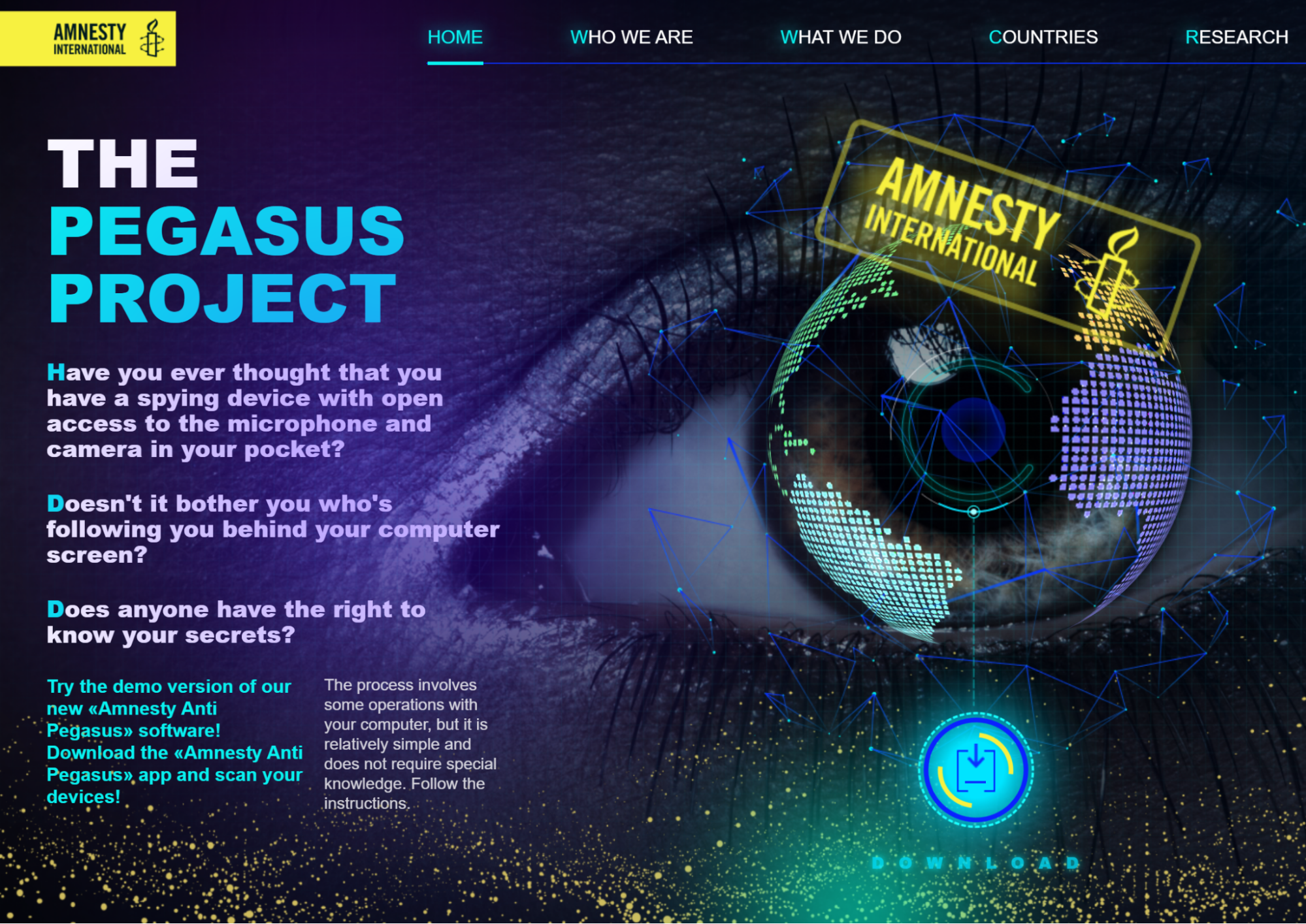
A wolf in sheep's clothing: Actors spread malware by leveraging trust in Amnesty International and fear of Pegasus

BEWARE! You may lose your money as new malware SharkBot wreaks havoc, attacks banking apps on smartphones

A new money-stealing malware makes rounds on Google Play Store posing as an innocent app with over 50,000 downloads - NotebookCheck.net News